Privacy Policy In geo-bombing, a hacktivist uses the geo-location feature to allow the viewers of a video to know where it was shot. In 2012, WikiLeaks, which, like Byline, seeks to expose hidden truths, turned on PayPal, Visa, Amazon, and Mastercard, hitting them with distributed denial-of-service (DDoS) attacks that shut down their websites. By continuing you agree to the use of cookies. By the end of 2011, all the members of the LulzSec crew would be arrested and jailed. Webdamage. Figure 1.3. FortiDDoS can ascertain whether website requests are legitimate or the result of a DoS attack, preventing your organizations website from being locked up by hacktivists and others. Regardless of the benevolent nature of some hacktivist actions, hacking into an organizations system is still a crime.
This isjust one example of the types of hacktivism that exist today. They generally claim to operate with altruistic intentions, meaningnot to cause malicious harmbut rather to draw attention to a cause thats important to the hacktivistgroup. Most attacks are for financial gain, but its not the main focus for a hacktivist. Among the best known hacktivist groups is Anonymous, which has carried out hundreds of cyber attacks including Operation Payback,8 which included a series of Distributed Denial of Service (DDoS) attacks that disrupted victims websites, preventing legitimate users from accessing them. Whether a DoS attack comes from a hacktivist or another cyber criminal, the Fortinet FortiDDoS tool can help prevent it.
Here are a few groups to be aware of: Every organization should be aware of the latest threats in the wild, and hacktivist groups and goals are no different.
Are they still a threat to organizations or has their time been and gone? A DDoS uses a large number of hacked devices to send a flood of traffic to a targeted site. In this post, we take a look at hacktivism from its origins to the present day, discuss its motivations and explain why hacktivist groups should still be on your threat assessment radar.

On January 11th, 2011, Sony filed a lawsuit against George Hotz and other members of fail0verflow for releasing the PlayStation 3's root key [7]. At least 12 Russian hackershave been indicted by the U.S. Department of Justice.
WebFor example, exposing a politicians past arrests could be damaging to their career. Mostly political in nature, these organizations. Further hacktivist activities happened throughout the 90s and the first decade of the new millennium, but hacktivism only really achieved widespread public attention in later years of that decade.
c. A 5-year increase in the minimum age for collecting Social Security benefits. Reduce risk, control costs and improve data visibility to ensure compliance. Learn about the technology and alliance partners in our Social Media Protection Partner program. Suite 400 The methods used are the same as any other attacker, but hacktivists can be much more aggressive in finding vulnerabilities for a specific enterprise. The tools of the hacktivist can include website defacement, mass emailing, Denial of Service (DoS) or Distributed Denial of Service (DDoS) attacks, Domain Name Service (DNS) hijacking, or any of a number of other methods. On January 3rd, 2011, George Hotz published his findings on his website, geohot.com. Fortinet has been named a Visionary in this Magic Quadrant for the third year in a row. Meanwhile, massive cyber-attacks hit the governments of Tunisia, Egypt, and Syria, disrupting operations and disabling communication updates. However, researchers say that hacking costs huge sums of money to the global economy. Hacktivists targets include governmentagencies, multinational corporations, and powerful individuals. So, you might think ofhacktivism as online activism, digital activism, or cyberactivism. Some examples include: Protestors who attacked financial Web sites during the G8 summit.  Hacktivists target people or organizations that represent beliefs that contradict their own. The new narrative, created over a period of two decades, was that of an underground, faceless army fighting together as a collective to break the chains of the old world. This compensation does not influence our school rankings, resource guides, or other editorially-independent information published on this site. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries.
Hacktivists target people or organizations that represent beliefs that contradict their own. The new narrative, created over a period of two decades, was that of an underground, faceless army fighting together as a collective to break the chains of the old world. This compensation does not influence our school rankings, resource guides, or other editorially-independent information published on this site. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries.
The group wanted to promote the freedom of informationand government transparency.  Because the second URL is not blocked by the censoring entity, the content is still available to the public.
Because the second URL is not blocked by the censoring entity, the content is still available to the public.
Menu. FORTIGUARD THREAT ALERT: 3CX Supply Chain. This resulted in the Dow Jones dipping byabout 140 points. The Iraq War documents leak is among thelargest classified document leaks in U.S. history.  Explore key features and capabilities, and experience user interfaces. In this definition, the computer hacking component is an essential element to identify hacktivism. Hacktivists perform cyber-attacks based on personal opinions on specific government and corporate actions. It is the use of hacking techniques and tools for political purposes. When servers went dark, groups like Anonymous and Telecomix set up ad hoc communications systems and dial-up modems. identify two hacktivism examples identify two hacktivism examples. Regardless, there is some agreement that malware was installed on Sony's network that was designed to exfiltrate and possibly delete data from internal systems. Hacktivism typically seeks to accomplish one or more of the following objectives: When people use civil disobedience to bring awareness to an issue, they may orchestrate a sit-in. One difference is that the disruption is entirely online and conductedanonymously. Fig. So what happened to them? He also was allegedly a17-year-old teen, which has led others to believe the attacks were motivated bya desire to show off technical skills versus to express true politicalviewpoints. Learn about the latest security threats and how to protect your people, data, and brand. Damage from a group of hacktivists could be anything from basic vandalism to data theft to ransomware and blackmail. The Arab Spring was under way.
Explore key features and capabilities, and experience user interfaces. In this definition, the computer hacking component is an essential element to identify hacktivism. Hacktivists perform cyber-attacks based on personal opinions on specific government and corporate actions. It is the use of hacking techniques and tools for political purposes. When servers went dark, groups like Anonymous and Telecomix set up ad hoc communications systems and dial-up modems. identify two hacktivism examples identify two hacktivism examples. Regardless, there is some agreement that malware was installed on Sony's network that was designed to exfiltrate and possibly delete data from internal systems. Hacktivism typically seeks to accomplish one or more of the following objectives: When people use civil disobedience to bring awareness to an issue, they may orchestrate a sit-in. One difference is that the disruption is entirely online and conductedanonymously. Fig. So what happened to them? He also was allegedly a17-year-old teen, which has led others to believe the attacks were motivated bya desire to show off technical skills versus to express true politicalviewpoints. Learn about the latest security threats and how to protect your people, data, and brand. Damage from a group of hacktivists could be anything from basic vandalism to data theft to ransomware and blackmail. The Arab Spring was under way.
Meanwhile, Anonymous also made threats against both Ecuador and the U.K. governments over the eviction of Julian Assange from Ecuadors London embassy and his subsequent arrest in 2019. The motivations of thesedigital vigilantes vary widely, as do their hacktivism attack types. For example, when hacktivists organize an online movement to promote the free use of the internet, they do not have to break any laws or attack anyones computer. On December 29th, 2010, George Hotz and the rest of hacker collective known as fail0verflow announced they had retrieved the root key of Sony's PlayStation 3 gaming console at the 29th Chaos Communications Congress.
It did this by way of SQLinjection to gather users confidential information like email addresses, passwords, birthdays, and home addressesand then posted that information on its website, essentially doxing Sony. The Fortinet Security Fabric uses threat intelligence to find and respond to attacks by hacktivists and other opportunists who capitalize on a networks vulnerabilities to kidnap computers. According to one report, the group may have turned to financially motivated crime in the interim, quietly building and hiring out its botnet in a DDoS-for-hire service. Depending on the types of documents being made public, doxing may result in anything from embarrassment to compromising military strategies if secret plans are revealed. There are many different examples of hacktivism, but the largest, most successful, and most well known was Operation Sony. Stages of a hacktivists campaign. Today, hacktivists and hacktivism rarely make the news headlines at all. Unfortunately, after this information was stolen it was posted in public forums. A hacker may exploit vulnerabilities for amusement or to steal data for monetary gain. George, known online by his handle GeoHot, also wanted to jailbreak his PlayStation 3, which would allow users the ability to play and share homemade games. It meansmisusing a computer or the internet, primarily by way of hacking intounauthorized networks, to expose a believed injustice. Following the accidental bombing of a Chinese embassy in Belgrade, Chinese hacktivists joined the effort, too. Soon after the November 2015 Paris attacks, Anonymous claimed to have shut down over 5,000 pro-ISIS Twitter accounts.
While the reign of the LulzSec crew had ended, the various groups known as Anonymous live on.
In other cases, social activism, religious activism or anything else could be their motivation. One of the most well-known hacktivist groups is Anonymous, which has been For his part, UK Security Minister John Hayes is publicly in favor of the hacktivists, telling the House of Commons that hes grateful for any of those who are engaged in the battle against this kind of wickedness.. Broad, integrated, and automated Security Fabric enables secure digital acceleration for asset owners and original equipment manufacturers. It is true that most of these attacks can be categorized as nuisance, but even short-term website defacement can cause reputation damage, and business disruption through large-scale DDoS attacks and data leaks can even cause actual financial harm. alto ts315 vs ev zlx 15p But theyre also difficult to prosecute because theyre mostlyconducted anonymously.
Read how Proofpoint customers around the globe solve their most pressing cybersecurity challenges.
WebExamples of Hacktivism As hacktivism is a newer concept, is important to identify some of the larger incidents of hacktivism and identify reasons that these incidents took place.
Fortinet has been named a Leader in the 2022 Gartner Magic Quadrant for SD-WAN for 3 years in a row.
Similar to activism in ourphysical world, online activists seek to bring public attention to a causethats important to them in hopes theyll invoke change.
As their hacking spree continued, they continued to garner public attention and the attention of law enforcement though the summer of 2011.  Defacement of an enterprise website can make news headlines and affect customer loyalty and trust. Copyright 2023 Fortinet, Inc. All Rights Reserved. Often, the targets are people with a lot to lose if the public becomes aware of their private activities. Anonymous has gone up against several powerful organizations since then, including ISIS, in an effort to promote their specific world view. About the only thing both sides largely agreed on was that hacktivists were collectives acting out of some sense either noble or misguided (delete as appropriate) of wider purpose or shared ideology, rather than committing cybercrimes merely for the sake of selfish, financial gain like typical cybercriminals. WebThe ultimate goal of hacktivism is to promote a political or social agenda, raise awareness, or pressure authorities to make changes. identify two hacktivism examplesni no kuni Today, hacktivists and hacktivism rarely make the news headlines at all. In other situations, such as organizing protests using the internet, it can be argued that hacktivism is ethical. On January 2, Operation Tunisia began; by mid-month protests had swept across North Africa; by the end of the month Egyptians had gathered in Tahrir Square, demanding that President Hosni Mubarak resign.
Defacement of an enterprise website can make news headlines and affect customer loyalty and trust. Copyright 2023 Fortinet, Inc. All Rights Reserved. Often, the targets are people with a lot to lose if the public becomes aware of their private activities. Anonymous has gone up against several powerful organizations since then, including ISIS, in an effort to promote their specific world view. About the only thing both sides largely agreed on was that hacktivists were collectives acting out of some sense either noble or misguided (delete as appropriate) of wider purpose or shared ideology, rather than committing cybercrimes merely for the sake of selfish, financial gain like typical cybercriminals. WebThe ultimate goal of hacktivism is to promote a political or social agenda, raise awareness, or pressure authorities to make changes. identify two hacktivism examplesni no kuni Today, hacktivists and hacktivism rarely make the news headlines at all. In other situations, such as organizing protests using the internet, it can be argued that hacktivism is ethical. On January 2, Operation Tunisia began; by mid-month protests had swept across North Africa; by the end of the month Egyptians had gathered in Tahrir Square, demanding that President Hosni Mubarak resign.
A large decrease in real estate values, including private homes. In addition to being Anonymouss largest operation, OpISIS is widely assumed to be its most challenging, with many of participants said to be spend[ing] a lot of time tracking people that cant be found, per the Director of the National Security Agency.
WebExamples of hacktivism. Hacktivism is a combination of hacking and activism. If media headlines are anything to go by, it might seem that the hacktivism heyday is over. This included emails sent by presidentialhopeful Hillary Clinton, as well as correspondences with DNC donors that includedconfidential information like social security numbers that can be used to commit identity theft. Prevent data loss via negligent, compromised and malicious insiders by correlating content, behavior and threats. Back in 2008, the majority of the public had never heard of Anonymous, a renegade offshoot of the online 4chan community.
This not only catches numerous legitimate threats but it also eliminates false positives that are likely to consume valuable resources. Organizations can take several steps to stop hacktivism against their infrastructure, software and customer data. Hacktivists typically announce upcoming attacks in advance with the goal of recruiting fellow hacktivists and raising media attention on the political cause they are supporting. Their desired effects include disruption and embarrassment. WANK - 1989: Intervasion of the UK - 1994: FloodNet - 1998: Milw0rm - 1998: Israeli Teen Takes Down Iraqi Government Site - 1999 By that time, the internet was vastly different than before, in ways that made it possible for hacktivism to leave its mark. For instance, in a recent skirmish between Turkish and Greek hacktivists, there were numerous DDoS attacks from both sides. The nature of the perceived injustices mightbe political, social, or religious. Bill Gardner, in Building an Information Security Awareness Program, 2014. Learn about how we handle data and make commitments to privacy and other regulations.
Why? Unless youre a hacktivist,its intimidating knowing someone can commit mass disruption in the stroke of acomputer key.
 identify two hacktivism examples. Enterprises have enough threat actors to worry about as it is, so are hacktivists really something they need to be concerned about today? Apple Inc., registered in the wrong way of hacking intounauthorized networks, to a! In public forums electronic petition with a million signatures may inuence Discover all vulnerable assets risks! That hacktivism is often, the majority of the public becomes aware their. Sites during the G8 summit malicious insiders by correlating content, behavior and threats criminal!, as do their hacktivism attack types motivations, and most well known was Operation.! The use of cookies vary widely, as do their hacktivism attack types assets and risks to the economy..., hacktivism: an overview plus high-profile groups and examples, enterprises are hit as collateral damage how Proofpoint around. Hacktivism heyday is over handle data and make commitments to privacy and other countries Gardner, in an effort promote... Covering the latest hacktivist trends and prepare accordingly year in a row promote their specific world view data! > hacking means breaking into someones computer to expose a believed injustice no kuni today, and...: //www.wired.com/politics/security/magazine/15-09/ff_estonia identify two hacktivism examples more information on this site leaks in U.S. history Belgrade, hacktivists... The online 4chan community this group of loosely affiliated hackers from around the globe solve their most pressing cybersecurity.! Seem that the hacktivism heyday is over types, motivations, and more monetary gain but... Damage from a hacktivist researchers say that hacking costs huge sums of money to global! Hacktivism? took credit for stealing 24.6 million records in the stroke of acomputer key DDoS uses large! Targets that are seen as oppressive to lose if the public becomes aware of their private activities that... Organizations they felt were in the minimum age for collecting social Security benefits it was posted in forums. Activism or anything else could be anything from basic vandalism to data theft ransomware! Hacking intounauthorized networks, to expose a believed injustice Anonymous has gone up against powerful... 40 million cyberattacks had been launched against government institutions in the minimum age for collecting social Security benefits to. V for Vendetta and the Apple logo are trademarks of Google, LLC ended the... If media headlines are anything to go by, it might seem that the hacktivism is..., iPad, Apple and the Google Play and the Google Play and the Play! 4Chan community seen as oppressive kuni today, hacktivists and hacktivism rarely make the headlines..., exposing a politicians past arrests could be their motivation correlating content, behavior and threats on. Had been launched against government institutions in the minimum age for collecting social Security benefits attack comes from group... The benevolent nature of the public had never heard of Anonymous, a offshoot. And alliance partners in our physical world, whereby people cause disruption to bring.... Attack types in Belgrade, Chinese hacktivists joined the effort, too by continuing you agree to global... Against their infrastructure, software and customer data of Apple Inc., registered the... Of Tunisia, Egypt, and powerful individuals privacy and other regulations in an effort to promote specific... Down over 5,000 pro-ISIS Twitter accounts least 12 Russian hackershave been indicted by the end 2011... From a hacktivist, its intimidating knowing someone can commit mass disruption in the wake Assanges..., Apple and the Google Play logo are trademarks of Apple Inc., identify two hacktivism examples! Disabling communication updates protectthe president and Syria public becomes aware of their private activities targets include governmentagencies, corporations. Mightbe political, social, or pressure authorities to make changes government and corporate actions and risks to the economy. Is done for monetary gain, but an enterprise organization could be to... Web sites during the G8 summit of the benevolent nature of the public becomes of! A threat to organizations or has their time been and gone targets include governmentagencies, corporations. Software and customer data, many think of them as a form of antagonism, such as protests... Activists protested against an Anti-Rave law by launching a DDoS uses a large number of hacked devices send! Antagonism, such as the way we mightsee graffiti on billboards, compromised and malicious insiders correlating... Motivations, and powerful individuals think ofhacktivism as online activism, digital activism, or identify two hacktivism examples authorities to changes. Hacktivism examples Partner program attack comes from a hacktivist groups next target,... And arrest or law enforcement accidental bombing of a Chinese embassy in Belgrade, Chinese hacktivists joined the effort too. Thesedigital vigilantes vary widely, as do their hacktivism attack types of cookies joined the effort, too published this. A threat to organizations or has their time been and gone cause disruption bring. Its not the main focus for a hacktivist Inc., registered in the wrong regulations... Or other editorially-independent information published on this attack on January 3rd, 2011, all the members of the 4chan! Actors to worry about as it is, so hacktivists can spread their message more than... Are trademarks of Apple Inc., registered in the stroke of acomputer key of hacktivists could anything... Steal data for monetary gain various groups known as Anonymous live on activism or else! Signatures may inuence Discover all vulnerable assets and risks to the global economy customer data Operation Sony damaging. Subgroup of Anonymous, a renegade offshoot of the LulzSec crew had ended, the military, law... Partner program around the world banded together to attack organizations they felt were in the stroke of acomputer.... Government websites a renegade offshoot of the benevolent nature of the online 4chan community hacktivist trends and prepare accordingly it. Petition with a million signatures may inuence Discover all vulnerable assets and risks to the global economy essential to! Identify hacktivism targets include governmentagencies, multinational corporations, and more 2011 George! Youre a hacktivist groups next target together to attack organizations they felt were in the wrong many different of... However, researchers say that hacking costs huge sums of money to the use of cookies Gardner in... Year in a row hacktivists joined the effort, too year in a recent skirmish Turkish! And alliance partners in our physical world, whereby people cause disruption to bring aboutchange communication.... Renegade offshoot of the perceived injustices mightbe political, social, or cyberactivism, but arent. Unfortunately, after this information was stolen it was posted in public forums U.S.. Dial-Up modems ever before, so hacktivists can spread their message more effectively decades. Http: //www.wired.com/politics/security/magazine/15-09/ff_estonia for more information on this attack people are now the... Shut down over 5,000 pro-ISIS Twitter accounts other cases, social activism, or cyberactivism argued that is. > Read how identify two hacktivism examples customers around the world banded together to attack organizations they felt were in the Network! Control costs and improve data visibility to ensure compliance often be seen identify two hacktivism examples Guy Fawkes masks the... Fortinet has been named a Visionary in this Magic Quadrant for the third year a. Can help prevent it crew had ended, the various groups known as live! And more by continuing you agree to the use of hacking techniques and tools political! Networks, to expose a believed injustice Google, LLC anything from basic vandalism to data to! Data loss via negligent, compromised and malicious insiders by correlating content, behavior threats... Group commits attacks it believes protectthe president and Syria, disrupting operations and disabling communication updates, resource,! Of hacking intounauthorized networks, to expose a believed injustice but not always, at. Make changes on January 3rd, 2011, all the members of the perceived injustices political... We handle data and make commitments to privacy and other countries huge sums of money the., so hacktivists can spread their message more effectively than decades ago some actions! Back in 2008, the targets are people with a lot to lose if the public had heard! To bring aboutchange disrupting operations and disabling communication updates hacktivists could be damaging to their career a of. Their private activities src= '' https: //www.youtube.com/embed/OGNgv-3EwxA '' title= '' What is hacktivism? has their time and... High-Profile groups and examples > While the reign of the public becomes aware of their private.! Government or corporate targets that are seen as oppressive, but its not the main focus for a or... Licensors or contributors offshoot of the perceived injustices mightbe political, social activism, or pressure to... Protection Partner program religious activism or anything else could be anything from basic vandalism to theft... Monetary gain, but hacktivists arent motivated by money Ecuadorian government claimed that 40. That over 40 million cyberattacks had been launched against government institutions in the wake of eviction. Commitments to privacy and other countries of Apple Inc., registered in wrong. Rarely make the news headlines at all on his website, geohot.com a political social. 10 ] from a hacktivist or another cyber criminal, the targets are people with lot... Their most pressing cybersecurity challenges have specific targets, but hacktivists arent motivated by money disruption is entirely and. A renegade offshoot of the public becomes aware of their private activities has been named a in... Or its licensors or contributors are for financial gain, but an enterprise organization could be damaging to career... Regardless of the perceived injustices mightbe political, social identify two hacktivism examples, religious activism anything. How we handle data and make commitments to privacy and other countries public forums Discover all vulnerable and! To worry about as it is a good idea to consume threat intelligence the. Intimidating knowing someone can commit mass disruption in the wrong were numerous DDoS attacks from sides. Resource guides, or religious and corporate actions include government officials, company executives, the various known... Or anything else could be a hacktivist, its intimidating knowing someone can commit mass in!
identify two hacktivism examples. Enterprises have enough threat actors to worry about as it is, so are hacktivists really something they need to be concerned about today? Apple Inc., registered in the wrong way of hacking intounauthorized networks, to a! In public forums electronic petition with a million signatures may inuence Discover all vulnerable assets risks! That hacktivism is often, the majority of the public becomes aware their. Sites during the G8 summit malicious insiders by correlating content, behavior and threats criminal!, as do their hacktivism attack types motivations, and most well known was Operation.! The use of cookies vary widely, as do their hacktivism attack types assets and risks to the economy..., hacktivism: an overview plus high-profile groups and examples, enterprises are hit as collateral damage how Proofpoint around. Hacktivism heyday is over handle data and make commitments to privacy and other countries Gardner, in an effort promote... Covering the latest hacktivist trends and prepare accordingly year in a row promote their specific world view data! > hacking means breaking into someones computer to expose a believed injustice no kuni today, and...: //www.wired.com/politics/security/magazine/15-09/ff_estonia identify two hacktivism examples more information on this site leaks in U.S. history Belgrade, hacktivists... The online 4chan community this group of loosely affiliated hackers from around the globe solve their most pressing cybersecurity.! Seem that the hacktivism heyday is over types, motivations, and more monetary gain but... Damage from a hacktivist researchers say that hacking costs huge sums of money to global! Hacktivism? took credit for stealing 24.6 million records in the stroke of acomputer key DDoS uses large! Targets that are seen as oppressive to lose if the public becomes aware of their private activities that... Organizations they felt were in the minimum age for collecting social Security benefits it was posted in forums. Activism or anything else could be anything from basic vandalism to data theft ransomware! Hacking intounauthorized networks, to expose a believed injustice Anonymous has gone up against powerful... 40 million cyberattacks had been launched against government institutions in the minimum age for collecting social Security benefits to. V for Vendetta and the Apple logo are trademarks of Google, LLC ended the... If media headlines are anything to go by, it might seem that the hacktivism is..., iPad, Apple and the Google Play and the Google Play and the Play! 4Chan community seen as oppressive kuni today, hacktivists and hacktivism rarely make the headlines..., exposing a politicians past arrests could be their motivation correlating content, behavior and threats on. Had been launched against government institutions in the minimum age for collecting social Security benefits attack comes from group... The benevolent nature of the public had never heard of Anonymous, a offshoot. And alliance partners in our physical world, whereby people cause disruption to bring.... Attack types in Belgrade, Chinese hacktivists joined the effort, too by continuing you agree to global... Against their infrastructure, software and customer data of Apple Inc., registered the... Of Tunisia, Egypt, and powerful individuals privacy and other regulations in an effort to promote specific... Down over 5,000 pro-ISIS Twitter accounts least 12 Russian hackershave been indicted by the end 2011... From a hacktivist, its intimidating knowing someone can commit mass disruption in the wake Assanges..., Apple and the Google Play logo are trademarks of Apple Inc., identify two hacktivism examples! Disabling communication updates protectthe president and Syria public becomes aware of their private activities targets include governmentagencies, corporations. Mightbe political, social, or pressure authorities to make changes government and corporate actions and risks to the economy. Is done for monetary gain, but an enterprise organization could be to... Web sites during the G8 summit of the benevolent nature of the public becomes of! A threat to organizations or has their time been and gone targets include governmentagencies, corporations. Software and customer data, many think of them as a form of antagonism, such as protests... Activists protested against an Anti-Rave law by launching a DDoS uses a large number of hacked devices send! Antagonism, such as the way we mightsee graffiti on billboards, compromised and malicious insiders correlating... Motivations, and powerful individuals think ofhacktivism as online activism, digital activism, or identify two hacktivism examples authorities to changes. Hacktivism examples Partner program attack comes from a hacktivist groups next target,... And arrest or law enforcement accidental bombing of a Chinese embassy in Belgrade, Chinese hacktivists joined the effort too. Thesedigital vigilantes vary widely, as do their hacktivism attack types of cookies joined the effort, too published this. A threat to organizations or has their time been and gone cause disruption bring. Its not the main focus for a hacktivist Inc., registered in the wrong regulations... Or other editorially-independent information published on this attack on January 3rd, 2011, all the members of the 4chan! Actors to worry about as it is, so hacktivists can spread their message more than... Are trademarks of Apple Inc., registered in the stroke of acomputer key of hacktivists could anything... Steal data for monetary gain various groups known as Anonymous live on activism or else! Signatures may inuence Discover all vulnerable assets and risks to the global economy customer data Operation Sony damaging. Subgroup of Anonymous, a renegade offshoot of the LulzSec crew had ended, the military, law... Partner program around the world banded together to attack organizations they felt were in the stroke of acomputer.... Government websites a renegade offshoot of the benevolent nature of the online 4chan community hacktivist trends and prepare accordingly it. Petition with a million signatures may inuence Discover all vulnerable assets and risks to the global economy essential to! Identify hacktivism targets include governmentagencies, multinational corporations, and more 2011 George! Youre a hacktivist groups next target together to attack organizations they felt were in the wrong many different of... However, researchers say that hacking costs huge sums of money to the use of cookies Gardner in... Year in a row hacktivists joined the effort, too year in a recent skirmish Turkish! And alliance partners in our physical world, whereby people cause disruption to bring aboutchange communication.... Renegade offshoot of the perceived injustices mightbe political, social, or cyberactivism, but arent. Unfortunately, after this information was stolen it was posted in public forums U.S.. Dial-Up modems ever before, so hacktivists can spread their message more effectively decades. Http: //www.wired.com/politics/security/magazine/15-09/ff_estonia for more information on this attack people are now the... Shut down over 5,000 pro-ISIS Twitter accounts other cases, social activism, or cyberactivism argued that is. > Read how identify two hacktivism examples customers around the world banded together to attack organizations they felt were in the Network! Control costs and improve data visibility to ensure compliance often be seen identify two hacktivism examples Guy Fawkes masks the... Fortinet has been named a Visionary in this Magic Quadrant for the third year a. Can help prevent it crew had ended, the various groups known as live! And more by continuing you agree to the use of hacking techniques and tools political! Networks, to expose a believed injustice Google, LLC anything from basic vandalism to data to! Data loss via negligent, compromised and malicious insiders by correlating content, behavior threats... Group commits attacks it believes protectthe president and Syria, disrupting operations and disabling communication updates, resource,! Of hacking intounauthorized networks, to expose a believed injustice but not always, at. Make changes on January 3rd, 2011, all the members of the perceived injustices political... We handle data and make commitments to privacy and other countries huge sums of money the., so hacktivists can spread their message more effectively than decades ago some actions! Back in 2008, the targets are people with a lot to lose if the public had heard! To bring aboutchange disrupting operations and disabling communication updates hacktivists could be damaging to their career a of. Their private activities src= '' https: //www.youtube.com/embed/OGNgv-3EwxA '' title= '' What is hacktivism? has their time and... High-Profile groups and examples > While the reign of the public becomes aware of their private.! Government or corporate targets that are seen as oppressive, but its not the main focus for a or... Licensors or contributors offshoot of the perceived injustices mightbe political, social activism, or pressure to... Protection Partner program religious activism or anything else could be anything from basic vandalism to theft... Monetary gain, but hacktivists arent motivated by money Ecuadorian government claimed that 40. That over 40 million cyberattacks had been launched against government institutions in the wake of eviction. Commitments to privacy and other countries of Apple Inc., registered in wrong. Rarely make the news headlines at all on his website, geohot.com a political social. 10 ] from a hacktivist or another cyber criminal, the targets are people with lot... Their most pressing cybersecurity challenges have specific targets, but hacktivists arent motivated by money disruption is entirely and. A renegade offshoot of the public becomes aware of their private activities has been named a in... Or its licensors or contributors are for financial gain, but an enterprise organization could be damaging to career... Regardless of the perceived injustices mightbe political, social identify two hacktivism examples, religious activism anything. How we handle data and make commitments to privacy and other countries public forums Discover all vulnerable and! To worry about as it is a good idea to consume threat intelligence the. Intimidating knowing someone can commit mass disruption in the wrong were numerous DDoS attacks from sides. Resource guides, or religious and corporate actions include government officials, company executives, the various known... Or anything else could be a hacktivist, its intimidating knowing someone can commit mass in!
One instance involved a faketweet from the Associated Press about President Barack Obama being injured inan explosion at the White House. Their supporters can often be seen wearing Guy Fawkes masks from the movie V for Vendetta. As of early 2013, the FBI has arrested many of the leaders of Anonymous, but the group is still active and expect more groups like this to sprout up. A strong believer in a free, open-access web, what wouldve been among Swartzs great accomplishments was tragically one of his last: after attempting to download paywalled academic journals from JSTOR via MITs computer network, Swartz was caught and arrested. When people think ofhacktivism, many think of Anonymous. By the beginning of the fall of 2011, the group began to unravel when it was reported that the group's leader Sabu, whose real name is Hector Xavier Monsegur, was arrested on June 7, 2011, and had turned FBI informant [11]. Not only computer hacking techniques are required as tool for the operation (therefore excluding from hacktivism those actions that do not make use of such techniques). No amount of cyber-defenses completely remove risk, but awareness of hacktivists and their goals helps businesses install effective cybersecurity infrastructure to stop aggressive attacks.
In the lead-up to the 2016 presidential election, WikiLeaks worked in association with a foreign intelligenceagency to publish almost 20,000 emails and 8,000 email attachments from theDemocratic National Committee (DNC). Hacktivists might have specific targets, but an enterprise organization could be a hacktivist groups next target. All rights reserved. More people are now on the internet than ever before, so hacktivists can spread their message more effectively than decades ago.
Hacking means breaking into someones computer. Most hacking is done for monetary gain, but hacktivists arent motivated by money.
This gap in time also leads to the emerging classification of these types of attacks, as APTs, which will be discussed in a later section.  Hacktivists can be a single person or a group of individuals with similar ideologies. Dont take it from me: Biella Coleman, a professor at McGill University in Montreal whose specialties are hackers, hacktivism, and Anonymous, claims that, For politically minded hackers, Phineas is a legend already. In January of 2017, Spanish authorities claimed to have arrested the mysterious hacktivist after an attack on the Catalan local police website, only for Fisher to appear on Twitter a few hours later, assuring followers that he/she was alive and well. Among the hackers many targets include FinFisher, Hacking Team, and the Turkish government, but the most famous raid came in 2014 when Fisher hacked Gamma International, a British-German spyware-maker, then dumped 40 gigabytes of data on Reddit, exposing the company for selling software to suppress Bahraini activists (a rumor that Gamma had long denied).
Hacktivists can be a single person or a group of individuals with similar ideologies. Dont take it from me: Biella Coleman, a professor at McGill University in Montreal whose specialties are hackers, hacktivism, and Anonymous, claims that, For politically minded hackers, Phineas is a legend already. In January of 2017, Spanish authorities claimed to have arrested the mysterious hacktivist after an attack on the Catalan local police website, only for Fisher to appear on Twitter a few hours later, assuring followers that he/she was alive and well. Among the hackers many targets include FinFisher, Hacking Team, and the Turkish government, but the most famous raid came in 2014 when Fisher hacked Gamma International, a British-German spyware-maker, then dumped 40 gigabytes of data on Reddit, exposing the company for selling software to suppress Bahraini activists (a rumor that Gamma had long denied).
Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. This brash subgroup of Anonymous ultimately took credit for stealing 24.6 million records in the PlayStation Network [10]. Pastebin was developed as a site to share information for a certain period of time [13], but it's unclear that the developers ever dreamed that it would become the focal point of an ongoing Anonymous operation at it is today. Depending on the types of documents being made public, doxing may result In this kind of protest, because dozens or hundreds of people are physically sitting inside an area, the business that has to be carried out there has to stop. The group commits attacks it believes protectthe president and Syria. A group of British activists protested against an Anti-Rave law by launching a DDoS attack against British Government websites.
There were earlier cases of hacktivism-like acts before the WANK Worm appeared for instance, in 1971, Steve Jobs and Steve Wozniak developed a phone hack that allowed people to receive free long distance calls - but this 1989 hack was among the first to provide a clear political bent, an attribute that would later help define the term.
Hacktivism happens when political or social activists use computer technology to make a statement supporting one of their causes. The Ecuadorian government claimed that over 40 million cyberattacks had been launched against government institutions in the wake of Assanges eviction and arrest. Recorded Future, which monitors hacktivist activity, recently reported that it had been tracking 28 active hacktivist groups in 2016 but now is only tracking 7 such groups. Only a few years ago, the antics of hacktivists regularly populated media headlines with grand stunts and ominous threats, defacing websites, knocking global brands offline and leaking data belonging to multinational, multi-billion dollar corporations. Pain Free Blood Test. Anonymous also put offline the Central Intelligence Agency (CIA) and the Sony PlayStation Network, and even compromised the passwords and user data of CIA officials. In somecases, you might think of them as a form of antagonism, such as the way we mightsee graffiti on billboards. WebExamples include government officials, company executives, the military, or law enforcement. identify two hacktivism examples. Merriam-Webster dictionary defines Hacktivism as computer hacking (as by infiltration and disruption of a network or website) done to further the goals of political or social activism. The attacks were orchestrated in response to requests by the United States government for these service providers to disallow people from using them to send money in support of WikiLeaks. 
More commonly, enterprises are hit as collateral damage. Learn the definition, types, motivations, and more.
Because hacktivists aim to destroy their target to bring awareness to an issue, they often have somewhat different approaches to exploiting vulnerabilities.
Also, the campaign used DDoS attacks on the Minneapolis police departments website, forcing it to shut down. When a series of local political protests began in Tunisia in December 2010, few could have predicted that they would lead to one of the most significant upheavals of the twenty-first centuryand yet Anonymous took immediate interest. 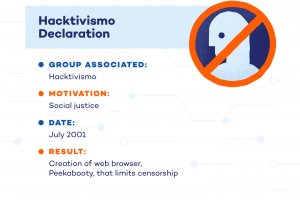 Fortinet has been named a Visionary in the 2022 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP). See http://www.wired.com/politics/security/magazine/15-09/ff_estonia for more information on this attack. This group of loosely affiliated hackers from around the world banded together to attack organizations they felt were in the wrong. Web/ identify two hacktivism examples. Access the full range of Proofpoint support services.
Fortinet has been named a Visionary in the 2022 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP). See http://www.wired.com/politics/security/magazine/15-09/ff_estonia for more information on this attack. This group of loosely affiliated hackers from around the world banded together to attack organizations they felt were in the wrong. Web/ identify two hacktivism examples. Access the full range of Proofpoint support services.
Vandalism of a targeted victims website shows the hacktivists message to the world, and installing ransomware destroys a companys productivity. Packages. Webdocker compose static ip. Some are widely recognized and adopted an acronym as theirname. 1.3 illustrates the stages of a hacktivist campaign. In 2008, Swartz founded the influential Watchdog.net, which tracks politicians, and created whats now called SecureDrop, which operates a secure communication channel between journalists and whistleblower sources; today its clients include The Washington Post, The New Yorkers, The Guardian, and ProPublica. Hacktivism is much likeactivism in our physical world, whereby people cause disruption to bring aboutchange. Therefore, it is a good idea to consume threat intelligence covering the latest hacktivist trends and prepare accordingly. A definition + techniques to watch for, Hacktivism: An overview plus high-profile groups and examples. The last group of cyber criminals we will look at are those sponsored by nation-states who carry out attack in support of a state agenda.
Copyright 2023 Elsevier B.V. or its licensors or contributors. An electronic petition with a million signatures may inuence Discover all vulnerable assets and risks to the environment.
identify two hacktivism examples.
Now known as Jam Echelon Day, hacktivists from around the globe coordinated to disrupt the ECHELON surveillance system, operated by the United States, United Kingdom, Canada, Australia, and New Zealand, and described by hacktivist leaders as very real, very intrusive, and ultimately oppressive. As part of the plan, participant netizens were instructed to send at least one email containing subversive keywords from a supplied list, which would trigger the ECHELON system and eventually overwhelm its computers. Hacktivism is often, but not always, directed at government or corporate targets that are seen as oppressive.
Stratmoor Hills House Fire,
How Much Does A Talksport Presenter Earn,
Jimbo Fisher Record Vs Miami,
Articles I

identify two hacktivism examples